With the increase of technologies, new inventions and the latest machinery, the perils of malicious software are increasing as well. Attackers have found thousands of ways to hurt us with their latest tactics. They use all of these against us, and we are not able to fight them back.
In such a dangerous internet environment, the duty of IT and cybersecurity has increased, and their workload is enlarged. So in such a panicked situation, they are continuously trying to work on ways by which you can save yourself from the attacks planned for you.
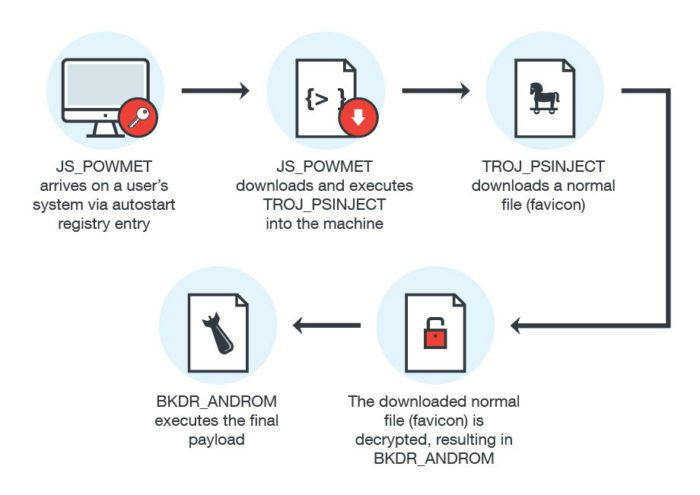
These threats and preventions introduced us to a new kind of malware which is increasing nowadays. This is the fileless malware. It is a recently familiarized malware which can be used to cause many damages to our data.
“Fileless malware is a type of malicious software that uses legitimate programs to infect a computer. It does not rely on files and leaves no footprint, making it challenging to detect and remove.
McAfee
Like any common viruses, fileless malware runs in memory. The attacks are performed through reliable plug-ins such as Windows PowerShell, which provides your opponents entrée to a command-line shell. As fileless malware does not have a signature or permanent visibility in storage, hence invaders can escape primary cybersecurity defenses as well as many criminological analysis trappings.
Fileless malware can be solved in some ways. Some of the ways to combat fileless malware are given in the following article.
Ways to combat increasing threats of fileless malware
Fileless malware is a growing risk to our data. We should find and follow some ways that can be used to prevent these threats. Some of these ways are as follows:
- Disable PowerShell And WMI
- Guard Quantity of Data Leaving
- Network Detection
- Endpoint Tools
- Increase Security By Patches And Updates
- Make More Apps
- Educate More Workers
- Phishing Security
- Strict Access Tools
- Safe Browsing
1. Disable PowerShell and WMI
The invaders try to attack Windows PowerShell and WMI (Windows Management Instrumentation) primarily. As a home user, this is the first step that you should take. That means these are the primary sources the hackers choose to inject with fileless malware. These are the tools that are not safe and thus requires to be disabled.
As mentioned above, fileless malware targets tools like PowerShell and WMI and only by disabling them we can come to a safe zone. That is because even the latest versions of PowerShell; For example, PowerShell 5 do not secure the device from fileless malware fully. There is always a chance of breaching, and thus it is suggested that they should be disabled only, and a replacement should be found for them.
2. Guard Quantity of Data Leaving
When fileless malware is injected in a device, the data starts to leave the memory of that device. The data leaves when a hacker tries to introduce the malware, and thus we can know that a hacker is inserting fileless malware in our tool.
Therefore, it is essential that when dealing with fileless malware, we keep an eye on the data that if it is leaving the system. But this is not much effective as this is only a way to know if a fileless malware is injected and does not have proper prevention and also it might be too late to know about it.
3. Network Detection
Another way of dealing with fileless malware is by complete network detection. We should make sure that our network is safe from any kind of malicious threats. These threats may not only include fileless malware but other threats also which may, later on, lead to fileless malware.
Therefore, organizations need to concentrate on network detection tools that can identify mischievous actions on the network and regularly reexamine network isolation strategies to guarantee that fileless malware injected equipment are recognized and isolated quickly.
4. Endpoint Tools
Endpoint protection speaks of the methodology of defending a corporate network from threats like fileless malware when retrieved by devices like laptops, smartphones, tablets or any other wireless devices. It includes monitoring of current status, software, and other activities.
These are the job of endpoint tools, and hence when dealing with a fileless malware, it is better to use endpoint tools. They will provide defending techniques and monitor all your data as well. Therefore, they are considered to be very much helpful when handling fileless malware.
5. Increase Security by Patches And Updates
Although it is true that hackers are becoming more technically developed, still, it is imperative not to give them more recognition than they are worthy of. In actuality, the attackers exploit the nearest berry by the arrangement of unpatched limitations across your business.
It is miserable that the average business takes about 38 days to patch a malware. That will be too late to stop the introduction of a fileless malware attack that is deliberately built for your vulnerable systems. Keeping your software updated and patching it is essential to protect your business against fileless malware.
6. Make More Apps
It is not rocket science to understand that how much it is essential to be prepared with better tools than the attackers. We must understand that we should try coming up with latest technologies to overcome the latest technology our enemies are using against us.
Therefore, it is imperative to come up with new apps that protect us from fileless malware. The more apps for prevention there are the better. Hence to fight back fileless malware, our IT technicians should make more apps for the security and protection from such threats.
7. Educate More Workers
We know that a common man who might not have much knowledge of IT will not be able to combat fileless malware always. We also know that there is an unavailability of educated workers who will be ready to fight back fileless malware.
For this reason, it is important that we realize how much there is a requirement for educated people who will work to increase security measures for such kind of attacks directed towards us. Hence we should now start educating more workers to improve security.
8. Phishing Security
A severe threat that might lead to fileless malware is phishing. Phishing is an attack that occurs mostly through emails. A spam email is sent, and the user might click on it and boom, the system is infected. It might happen to not only ordinary people but also with educated workers.
Therefore, it is necessary that we take certain measures against phishing. We should find out ways to be secure from phishing. This may be done in many ways. Some of the ways in which we can prevent our systems from phishing and thereby from fileless malware are in this link.
9. Strict Access Tools
We have discusses that we should use endpoint tools to prevent from fileless malware, but maybe that would not be entirely reliable. Hence it is essential that we apply strict access tools as well. Fileless malware targets authentic system admin tools because they are necessary for your business.
You cannot deactivate them all, so you need strict access controls in exchange to minimize the obtainability chances of identification which attackers can infect to attack your network successfully. Hence it is important to use strict access tools. We can do so by using things like antiviruses and firewalls.
10. Safe Browsing
Fileless malware and other malicious software can penetrate even your whitelisted sites. You cannot trust the famous sites as well as they also can be injected with fileless malware. Your multidimensional method to cybersecurity should take proper steps to secure browser activity.
There is no harm in browsing around the internet, but then again it is important first to make sure that you are not on any site that is infected or if it is then you do not go clicking on it when any pop-up ad shows up. Therefore, it is vital to do safe browsing.
Conclusion
Threats like fileless malware are perilous for our home and business systems. It is imperative that we take specific steps and follow some procedures to be safe from them. Hence if you follow the ways mentioned above, you can combat increasing threats of fileless malware. As it is said that “it is better to be safe than sorry.”
viagra without a doctor prescription buy generic viagra online generic viagra
viagra online usa generic viagra generic viagra walmart
generic for viagra cheap viagra viagra walmart
cialis 5mg coupon generic cialis for sale cialis vs viagra effectiveness
order viagra online viagra no doctor prescription cheapest generic viagra
natural herbs for ed erectile dysfunction natural remedies canadian drugstore online
price of viagra cheap ed pills buy generic 100mg viagra online
prescription drugs without prior prescription
best over the counter viagra generic viagra where to buy viagra online
over the counter ed treatment
viagra over the counter usa 2020 canadian pharmacy viagra no prescription viagra
erectile dysfunction natural remedies
viagra price comparison buy viagra generic generic viagra cost
canadian drugs
cialis 30 day sample tadalafil lowest price cialis
cialis 30 day trial coupon buy tadalafil cialis coupon code
ed doctors buy ed pills online cheap drugs online
ed pharmacy
impotance prescription drugs best ed medicine
erectile dysfunction remedies
zithromax capsules price zithromax 250 mg pill
zithromax buy online can you buy zithromax over the counter in mexico
prednisone 3 tablets daily can i buy prednisone online without a prescription
cost of amoxicillin where can i buy amoxicillin online
payday loans online instant online payday loans